The Development and Technology of Realview 4security
Realview 4security began in 2007 as a security data collection system developed at a client's request. This led to the creation of the MONITORING module. The core infrastructure was built using open-source code, leveraging Python and PHP technologies along with an ORACLE database. The software solution was delivered for operation in 2008.
In 2009, the HUMAN RESOURCES MANAGEMENT module was developed and integrated, enabling efficient management of security personnel, which had previously been maintained in Excel sheets. In both core modules, developers worked closely with professionals from the contracting company who had deep expertise in the operation of these systems. The result was both highly functional and cost-effective. At this stage, Realview 4security functioned as a hybrid of two software types: PSIM (Physical Security Information Management) and PM (Project Management), operating on a common database with direct correlation between software modules.
By 2016, the rise of mobile applications on the APPLE and GOOGLE app stores prompted Reform to acquire the app development company HummingTech Ltd, leading to the development of the iAlert Facility and iAlert PLUS apps. The first app was designed for employees of security companies, infrastructure patrols, as well as cleaning and maintenance personnel in hotels and public facilities. The second app was designed for universal use, providing a "Panic Button" for individuals facing immediate danger.
These applications were seamlessly integrated into the two core modules of Realview 4security, significantly enhancing the capabilities of Security Operations Center (SOC) managers through the PATROL module. They could now monitor real-time geographic locations of incidents, analyze incidents based on time and location, and cross-check them against an action plan in coordination with client instructions. This marked the activation of the DECISION MAKER module.
The transformation of Realview 4security into a SOAR (Security Orchestration, Automation, and Response) solution was successfully achieved, reinforcing its role in protecting human security and critical infrastructure.
Differences between PSIM, SOAR & SIEM software systems
|
Feature |
PSIM |
SOAR |
SIEM |
|
Primary Purpose |
Manages and integrates physical security systems (CCTV, access control, alarms). |
Automates, orchestrates, and responds to cybersecurity incidents. |
Collects, analyzes, and correlates security event data. |
|
Focus Area |
Physical security (e.g., cameras, access control, alarms). |
Cybersecurity threat response and automation. |
Real-time monitoring and log analysis. |
|
Data Sources |
Video surveillance, sensors, alarms, access logs. |
SIEM, threat intelligence, incident reports. |
Network logs, system logs, firewalls, IDS/IPS. |
|
Main Functions |
Centralizes and integrates security devices for better management and response. |
Automates incident response workflows and orchestrates security tools. |
Detects threats, analyzes logs, and generates alerts. |
|
Response Capabilities |
Human-driven response with decision support. |
Automated and semi-automated response. |
Provides alerts but requires manual intervention or SOAR integration. |
|
Key Benefit |
Improves situational awareness for physical security. |
Reduces response time and workload with automation. |
Detects and identifies threats using log data correlation. |
|
Example Use Case |
Integrating CCTV with alarms for real-time incident management. |
Automating phishing email investigation and response. |
Detecting and logging potential cyber threats from firewalls. |
How They Work Together
• SIEM collects and analyzes security event logs.
• SOAR automates incident response based on SIEM alerts.
• PSIM manages and integrates physical security infrastructure but does not deal with cybersecurity threats directlyThe next stage of technological superiority for Realview 4security began in 2019, as REFORM collaborated in the cloud sector with AMAZON and its AWS (Amazon Web Services) system. In the following years, three AWS technologies were integrated into Realview 4security, giving it world-class capabilities. The IaaS (Infrastructure as a Service) technology deployed Realview 4security on a global infrastructure capable of supporting any PSIM requirement, wherever it needed to operate. Issues related to data collection from alarm systems, sensors, and cameras could now be organized and resolved easily. In particular, network problems and communication with the operations center had now been overcome. The PaaS (Platform as a Service) technology enabled the ORACLE database to be located at any point of the client, with unparalleled response speed. Its security reached the highest level, and its maintenance transitioned to an "autonomous" response, drastically reducing the final cost for the client.
The third technology was an area of study in 2019, but in the following years, it set Realview 4security apart from competing technologies. This was the IoT (Internet of Things) technology, from which the IoT module was created. Since 2021, Realview 4security can now integrate any IoT device or camera and process it. It can upgrade the core operating system on multiple IoT devices with minimal involvement from the technical team or even act preventively or decisively by sending a command or an upgrade to immediately counter a cybercrime.
Through the integration of AWS security technologies (Machie, KMS, Security Hub, Security Lake) combined with Realview 4security’s fundamental capability to unify AWS infrastructures (OpenSearch, Splunk) and visualize data from them, it evolved into a fully equivalent SIEM (Security Information and Event Management) solution. Now, the company’s entire IT infrastructure can be processed and managed efficiently, with the primary goal of providing the Security Operations Center (SOC) with all the essential information it needs to be aware of.
With the recent (2024) integration of authentication technology, the IDENTITY VERIFICATION module was created within Realview 4security. Now, every alarm system, fire detection sensor, camera, or even IT equipment can be encrypted and authenticated, monitored, and upgraded to protect a client from cybersecurity incidents.
With Realview 4security, a SOC is now fully equipped to handle incidents with the precision required within just a few minutes, as mandated by the new NIS2 regulatory framework. The technology an SOC needs to focus on is complex, but Realview 4security provides the tools to create a shield for each of the 10 security sectors.
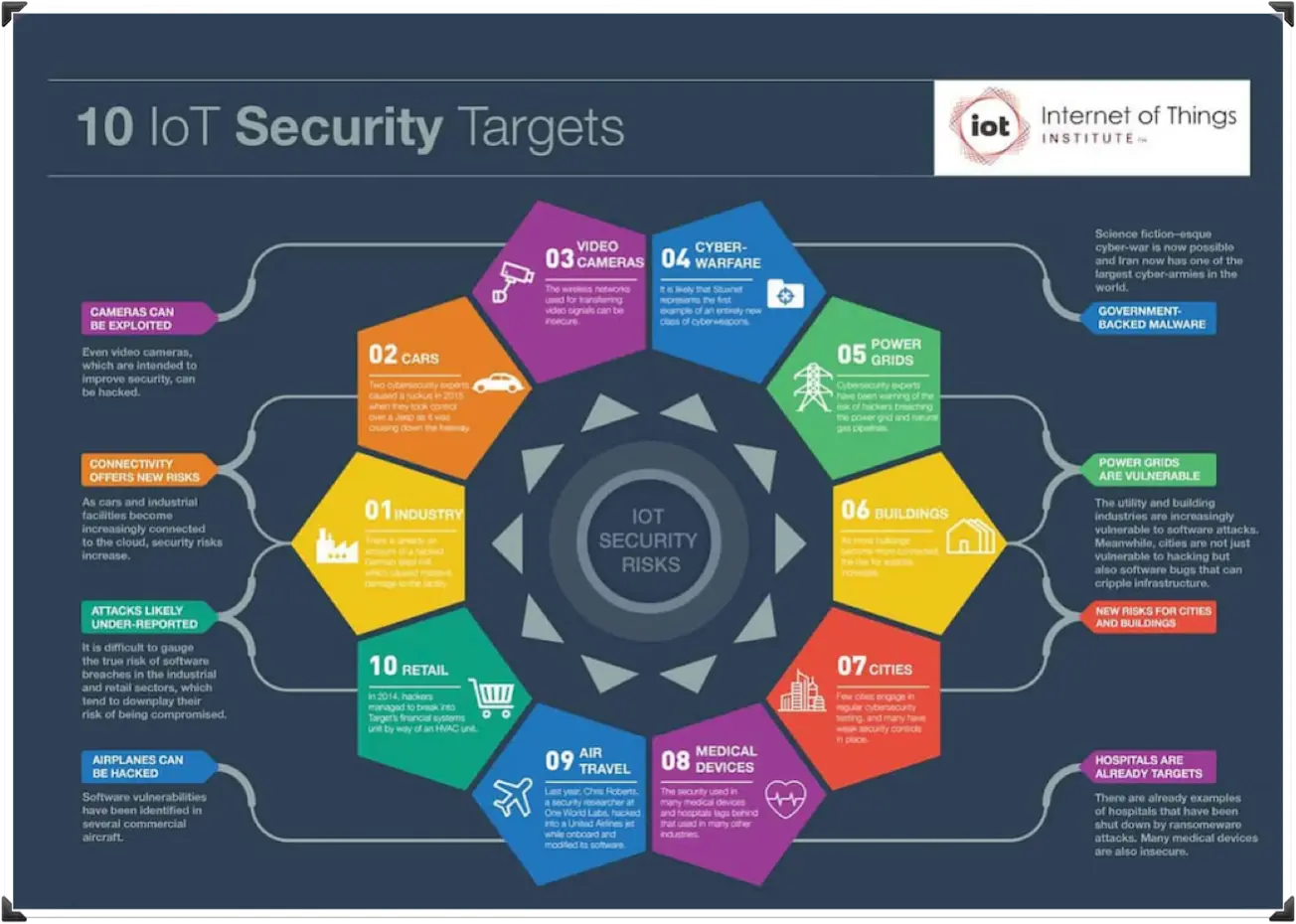
Through Realview 4security, clients, supervisors, and management can always stay informed about the status of security systems, whether they are currently implemented or will be in the future, as well as the methods of action. They can receive real-time updates on whether a system has been breached, if a security guard is heading to a specific checkpoint, all while monitoring from on-site cameras or even aerial devices (drones). The Security Operations Center (SOC) processes all suspicious intrusion signals, distress messages, threats, fire alerts, and medical emergencies, assessing any emerging issue and suggesting the optimal workflow and actions to the operator, ultimately aiming to accelerate the ideal resolution. Realview 4security is designed to fully organize companies’ efforts toward an accurate performance and quality control system.
The modules are defined as follows:
1. Monitoring Module

With this module, you gain a comprehensive overview of everything you manage, supported by AWS and enhanced with advanced Artificial Intelligence (AI) models. It collects, correlates, and presents data, ranging from complex environmental interactions to the resolution of intricate problems.
2. Human Resources Management Module
Built on solid foundations with over 15 years of expertise in the security sector, this module seamlessly integrates with
 your ERP software, facilitating the collection and interconnection of all personnel data. It works in coordination with workforce scheduling, the AI model, and the Patrol unit, providing real-time information on personnel location, activities, and even guiding them to their assigned work locations.
your ERP software, facilitating the collection and interconnection of all personnel data. It works in coordination with workforce scheduling, the AI model, and the Patrol unit, providing real-time information on personnel location, activities, and even guiding them to their assigned work locations.
3. Patrol Module

Manage patrol schedules, monitor staff locations, and check compliance with the correct order and duration of each visit. Perform historical audits and evaluate the results to ensure optimal performance and accuracy.
4. IoT Module

IoT management is simplified with the right software and backend services that ensure data encryption, device status monitoring, and the seamless deployment of updates. Realview 4security provides a comprehensive set of tools that enhance your operational capabilities.
5. Identity Verification Module

Verifying an application, a user, or even an IoT device can often be a complex and demanding task. Our module simplifies the process by integrating all verification needs into a single, comprehensive solution.
6. Decision Maker Unit

This module is designed to assess customer instructions and provide tailored responses effectively, filtered through AWS artificial intelligence.
Solution Completeness
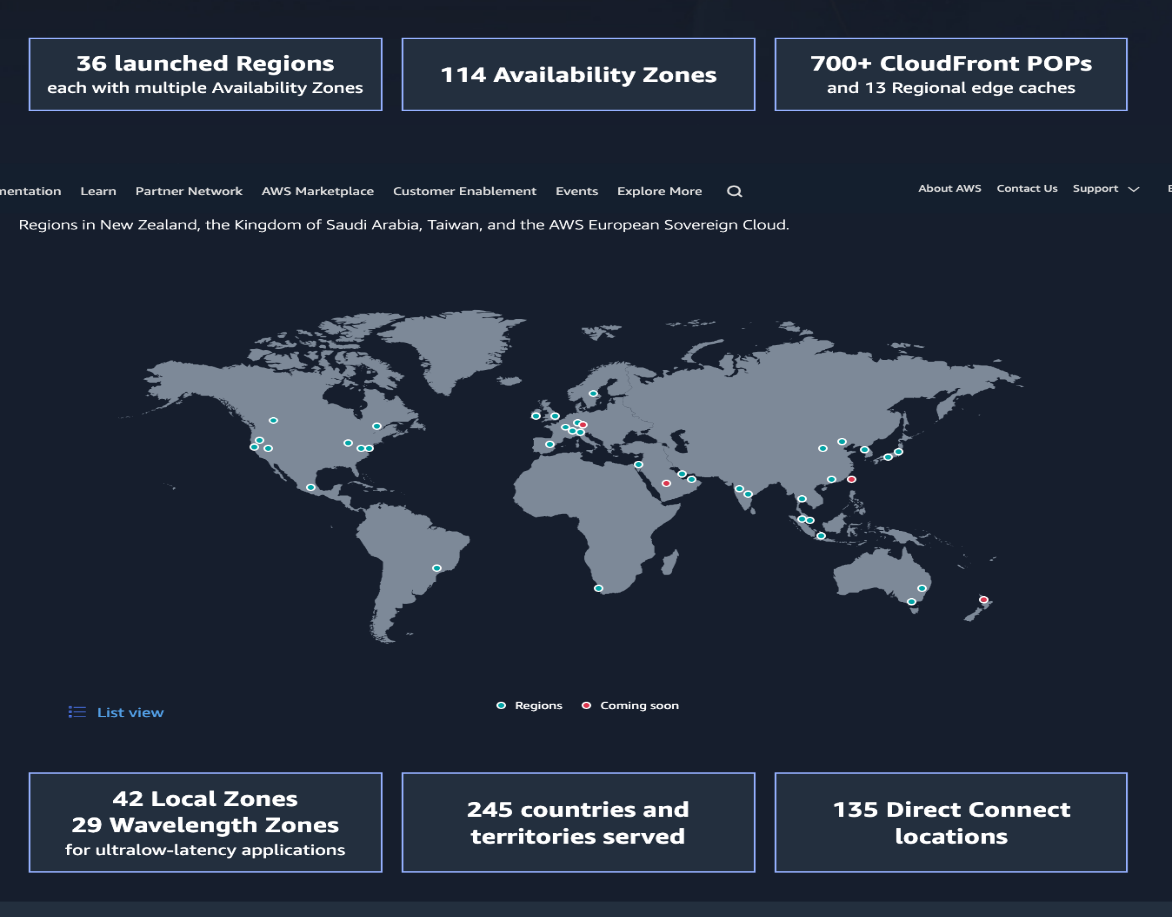
For the SOC and the integration of Realview 4security, no special equipment is required, such as servers, operating systems, signal receivers, specialized signal monitoring software, antivirus software, routers, firewall devices, technical support services, or large UPS and power installations. Nothing! All of these are already integrated into the Realview 4security platform and are available at your SOC location with a secure connection to AWS facilities that are available in 36 regions around the world. The option for a hybrid solution[3] is always offered if the customer desires it or if the end customer mandates it.
All Realview 4security solutions are available through a subscription model, with options for one, three, or five-year durations.
[3] A hybrid solution is one that combines on-premises infrastructure with cloud-based resources.
The Multidimensional Realview 4security
1st Dimension: Each module of Realview 4security is interconnected at the software code level. This is known as the core dimension. All data is stored in the world’s most powerful and secure database, encrypted end-to-end, and simultaneously resides in at least two (2) different AWS data centers.
2nd Dimension: The next dimension is the AWS infrastructure, where each module communicates with more than 80 AWS services to complete assigned tasks. The security, resilience, and connectivity of Realview 4security rely on this global technology, integrating all solutions into a cost-effective, instantly scalable structure with easily measurable expenses.
3rd Dimension: The third dimension is the support of the code and the entire Realview 4security solution, managed by a team of distinguished developers with years of expertise and certifications in the security field. It is complemented by AWS's extensive global support team, available in multiple languages, offering service agreements of up to 24x7x4.
4th Dimension: The fourth dimension of Realview 4security is provided and enriched by REFORM’s own clients. This enables interaction and collaboration between corporate entities seeking to exchange security services. Realview 4security securely and clearly consolidates essential employee records and system-related information, making them available for processing only for the necessary duration required by each corporate entity.
5th Dimension: With its multidimensional architecture, Realview 4security is built on open-source technology, giving clients full ownership of the code. This fifth dimension empowers clients to develop their own code components, proprietary solutions, and algorithms without concerns about losing intellectual property.
Below, the Realview 4security modules are analyzed in detail.
1. Monitoring Module

With this module, you gain a comprehensive visual perspective on everything you manage. Supported by AWS[4] and enhanced with advanced Artificial Intelligence (AI)[5] models, it collects, correlates, and presents data, ranging from complex environmental interactions to the resolution of intricate problems.
Essentially, this module fully equips your company's Security Operations Center (SOC)[6], which is responsible for monitoring facilities, personnel, or client systems. The operation of the SOC with Realview 4security, in combination with AWS, enables the integration of systems across multiple and diverse levels, allowing for the implementation of projects beyond any limitations.
Below, we provide a concise analysis of this module.
[4] AWS amazon web services
[5] AI artificial intelligence. (AI)
[6] SOC = Security Operations Center. Other names used worldwide include CLS (Central Alarm Receiving Center), CMS (Central Monitoring Station), IMS (Incident Management System), and others.
1.1 Signal Management
Signal Logging: Every signal received at the SOC is automatically logged into the system, including details such as the type of signal (e.g., intrusion alarm, fire, sensor threshold breach), the time of transmission and reception, the location, and the status of the entity that sent the signal.
Signal Analysis: Realview 4security analyzes each signal and links it to the corresponding projects or clients, providing reports that help managers monitor the status and efficiency of operations.
Immediate Response and Notification: When a signal is triggered, the system instantly notifies the responsible personnel to take appropriate action. If intervention is required for a client or security officer, the system alerts the appropriate supervisor.
1.2 System Management
Here, you can add and manage every device belonging to your client, such as alarm systems, video surveillance systems, location trackers, sensors, and IoT devices. Monitor, manage, and take immediate action for the benefit of your client. Realview 4security, in combination with AWS, enables the integration of multi-level and diverse systems, adding encryption even when not initially supported by the manufacturer.
Additionally, it allows for device monitoring and large-scale, regular updates of operating software, reducing operational costs while ensuring a high-security framework. This is crucial, as vulnerabilities in client security often originate from outdated or unmonitored devices.
1.3 Event Management
Event management serves as the interface between the system and human intelligence. The SOC administrators, the response team in the decision-making center, and field personnel interact with Realview 4security, receiving information and clearly documenting their actions. Here, you can process any command, whether originating from client instructions or artificial intelligence, and take the appropriate actions. The system allows you to add and manage all client events using predefined procedures, commands, or even ad hoc emergency response solutions.
Realview 4security, in combination with AWS, enables the integration of multi-layered systems, providing multidimensional visualizations on control center screens, automated phone calls to involved parties, or notifications and emails with critical action instructions.
Every event action and corresponding response is recorded in the central database, secured against any unauthorized modification, and stored for up to 10 years. Ultimately, this data remains accessible for management, security authorities, insurance companies, internal staff training, and even AI model training.
2. Human Resource Management Module

Built on solid foundations with over 15 years of expertise in the security sector, this module seamlessly integrates with your ERP[7] software, facilitating the collection and interconnection of all personnel data. It collaborates with workforce scheduling, the AI model, and the Patrol Unit, providing real-time information on employees' locations, activities, and even guiding them to their assigned workstations.
Proper and well-organized human resource management is essential for a company's efficient operation. Realview 4security ensures that employee registration and monitoring are conducted in the most effective and secure manner.
Below, we provide a brief analysis of this module.
[7] ERP enterprise resource planning.
2.1 Employee Registration Process
Initial Registration: Each new employee, security guard, or other staff member is entered into the Realview 4security database with all personal demographic details (name, address, phone number, photo, resume, etc.), as well as information regarding certifications and completed training programs.
Data Categories: Employees are categorized based on their specialization (e.g., security guards, coordinators, administrative staff, special skills, etc.) and other critical details, such as preferred working hours and required due diligence checks.
Training & License History: The system tracks each employee’s training history (e.g., first aid certifications, security licenses, etc.) and records the status of their leave (regular leave, sick leave, etc.), helping the company avoid additional costs associated with unused paid leave.
2.2 Human Resources Data
Reports & Monitoring: Managers can generate reports for each employee, including the number of working days, performance in training programs, delays, or errors in task execution. This information is integrated into the system and updated in real time.
Performance Evaluation: Employee performance assessments are recorded and used to improve training programs, recognize high-performing employees, and provide opportunities for career advancement.
2.3 Shift Management
Shift Scheduling: The HR manager assigns employee shifts, and Realview 4security ensures that each employee is scheduled according to company needs and availability. This scheduling is integrated into the system, guaranteeing optimal allocation of human resources.
Staff Replacement: In case of absence or unavailability, the system automatically notifies managers and suggests replacements, ensuring continuous operational coverage.
2.4 Operational Management
Efficient management of security programs and tasks operates on multiple dimensions, such as by client, project, contract, and post, ensuring the company's smooth and effective operation. Both the quality of work performed and the final labor costs are optimized. Realview 4security integrates all necessary functions for daily operations management as follows:
2.4.1 Task Registration and Monitoring
Work Scheduling: Every security task assigned to a guard or a security team is recorded in the system with all relevant details (date, time, location, client requirements). Each task is categorized accordingly and linked to the personnel executing it.
By Client and Project: Realview 4security enables tracking of each task by client and project. This allows managers to instantly monitor task progress and adjust plans based on client needs.
Report Generation: The system provides reports for each guard, contract, project, or client, detailing task execution, hours spent, potential violations or issues encountered, and necessary corrective actions.
2.4.2 Information Extraction and Performance Monitoring
Client Reports: The company can generate reports for each client, including security hours, costs, irregularities, and suggested improvements.
Guard Reports: The system tracks overall guard performance, analyzing task accuracy, client satisfaction, and potential mistakes or omissions in their duties.
Project Reports: Detailed task tracking per project allows the company to monitor performance at specific locations, improving organization and work scheduling.
2.5 Accounting Management
The accounting department is responsible for accurately recording working hours and appropriately invoicing clients. Realview 4security provides automated tools for tracking working hours to ensure correct invoicing. Data is exported to accounting and payroll software as follows:
2.5.1 Collection and Analysis of Working Hours
Time Recording: All working hours of security personnel are recorded in real-time, either manually or through automatic tracking via work check-in/check-out using mobile applications (such as iAlert Facility or other proprietary solutions) or other devices (on-site time-tracking systems).
Analysis and Categorization of Hours: Recorded hours are analyzed and categorized based on the type of work (e.g., cleaning, security, maintenance, training) and assigned to the respective client or project. This analysis allows accounting managers to accurately determine costs and plan invoicing accordingly.
2.5.2 Data Generation and Transmission
Client Billing: After consolidating working hours and corresponding rates, Realview 4security transmits the records to the accounting software for invoice generation.
Employee Payroll: By gathering recorded working hours, Realview 4security sends the data to the payroll system to facilitate salary processing.
Automated or Manual Data Transmission: The system can transmit data automatically at scheduled intervals or manually upon the administrator's request.
2.6 Material Management
Material management is crucial for the smooth operation of the Company's business activities. Proper tracking and recording of materials enable efficient resource management while ensuring that projects are completed without delays due to equipment or material shortages.
2.6.1 Material Debit & Credit
Material Registration: Materials (such as security equipment, office supplies, and maintenance materials) are recorded in the system with all necessary details: material description, quantity, unit price, supplier, and procurement date.
Material Debit & Credit Process: This process involves tracking materials used in each project or client. Depending on usage, materials are either charged to the client or monitored for internal company use. When consumed or utilized, inventory levels are updated in the system, and reports are generated detailing the quantity of materials used per project or client.
Material Reports: Realview 4security provides reports that allow material management personnel to monitor inventory levels, assess material needs, and schedule orders to replenish stock.
2.6.2 Material & Work Management
Equipment per Project: For each security or maintenance project, the system records the equipment and materials used and links them to the client or project. This allows the company to track material performance across various projects and evaluate them based on their usage duration and effectiveness.
Material Maintenance Management: The material manager can monitor the condition of equipment and materials in use and schedule necessary maintenance or repairs to ensure operational efficiency.
2.7 Tender Management
Everything starts here. The company participates in tenders for security, cleaning, or other service provisions for various organizations and businesses. Realview 4security provides tools to support the tender management department, facilitating bid preparation and tracking their progress efficiently.
2.7.1 Tender Management
Tender Registration: Every tender is recorded in the system with details such as date, client, tender requirements, and execution terms. This provides a comprehensive overview of all tenders in which the company participates while linking them with ongoing projects/contracts. A cost comparison is a key metric required by management.
Bid Preparation: The system allows for the creation, recording, and tracking of submitted bids. The tender management team uses Realview 4security to gather necessary data (material costs, labor hours, required personnel) and formulate bids based on each tender's specific requirements.
Tracking and Updates: The system provides notifications on bid submission deadlines and tender evaluation processes, ensuring no opportunities are missed and allowing real-time monitoring of tender progress.
2.8 ERGANI Information System and Legal Compliance
The governmental information system (IS) ERGANI is responsible for recording employees' working hours, ensuring compliance with labor laws, and managing payroll processes. Realview 4security provides tools for automatic work hour tracking, legal compliance, and seamless data communication with the ERGANI system.
According to the clarifying circular 37271/21-06-2024 regarding the digital work card, it is emphasized that for security service providers, the obligation to transmit work start and end timestamps to ERGANI can be fulfilled by 23:59 on the current day. This deadline applies to all submission methods, including form completion, XML file import, API submission, or Card Scanner use.
2.8.1 Work Time Management
In full compliance with the circular, the Realview 4security software organizes security personnel schedules, integrating real-time presence tracking at security posts using the iAlert Facility app installed on employees' mobile devices. This system allows the company's HR department to accurately process attendance and departures for each shift and employee. At the end of the day, it automatically submits the data to the ERGANI IS via API.
Work Hour Recording: Realview 4security logs security guards’ working hours, shifts, and overtime. The system enables immediate registration and monitoring of employee attendance, ensuring compliance with labor laws.
Work Hour Reports: The platform generates reports on work hours per guard, project, or client, offering a clear overview of time spent on each assignment. These reports provide valuable insights for both the company and its clients, ensuring full operational transparency.
2.8.2 Benefits
Time Savings: Automated work hour recording and seamless integration with the ERGANI system reduce administrative workload and ensure accurate and timely submissions.
Compliance with Labor Laws: Realview 4security helps the company stay compliant with labor regulations by ensuring correct work hour tracking and preventing issues with auditing authorities.
3. Patrol Module
 Efficient patrol management is crucial for the company, as regular and well-organized patrols ensure effective security and rapid response to incidents. Realview 4security provides advanced tools for recording, monitoring, and analyzing patrol activities.
Efficient patrol management is crucial for the company, as regular and well-organized patrols ensure effective security and rapid response to incidents. Realview 4security provides advanced tools for recording, monitoring, and analyzing patrol activities.
3.1 Patrol Management
Patrol Logging: Every patrol is recorded in the system, including the route, start and end times, and checkpoints visited by the security guard. The system links patrols to specific projects and clients to ensure full coverage of required areas.
Geolocation (GPS): Realview 4security utilizes GPS tracking to monitor patrol routes and exact locations in real time. This enables immediate alerts in case of route deviations or delays.
Patrol Reports: After completing each patrol, the system generates detailed reports, including the route taken, actions performed, observations, and any incidents or issues encountered. These reports are available for analysis by project or company managers.
3.2 Benefits of Patrol
Improvement of Patrol Management: Geolocation and detailed reports enable the improvement of patrol effectiveness, efficient use of resources, and monitoring of guard performance.
Reduction of Response Time: The ability to track patrols in real-time reduces response time to emergency incidents and ensures a quick reaction from the security team.
Enhancement of Transparency: Patrol reports provide complete transparency in the execution of tasks and facilitate service evaluation by clients.
3.3 Security
Here, you can manage patrol schedules, monitor staff locations, and check the sequence and duration of each visit. You can perform historical audits and evaluate results to ensure optimal performance and accuracy. Security is at the core of the Company's services in this section. The registration and monitoring of security tasks are carried out with precision and in real time through Realview 4security.
3.3.1 Security Management
Registration of Security Tasks: Security tasks are recorded in the system with a complete report on working hours, locations, and personnel involved in each task. The system integrates tools to monitor each client’s needs, corresponding working hours, and types of security services required.
Performance Evaluation: The security supervisor monitors the performance of security staff and the quality of their services through system-generated reports. These reports include the accuracy of security personnel in executing their duties, any irregularities, and suggested improvements.
Incident and Accident Management: The system enables the recording and tracking of accidents or other incidents, ensuring that appropriate procedures are followed to protect employee safety and notify the relevant authorities.
3.3.2 Security Safeguarding
Security is the foundation of the company's operations. Realview 4security and iAlert Facility collaborate to provide the most advanced tools for monitoring and managing the security of facilities, patrols, and employees.
3.3.3 Data Security
Data Protection: Both Realview 4security and iAlert Facility adhere to strict security protocols to protect customer and employee data. All information is stored in secure databases with encryption and protection against external threats.
Facility Security: Continuous monitoring of facilities through iAlert Facility ensures that premises remain secure and that any signs of danger (such as intrusions or fires) are detected immediately and addressed in a timely manner.
3.3.4 Personnel Security
Incident Monitoring: Realview 4security records every event related to personnel, from attendance tracking to managing accidents and emergency incidents. All events are monitored and evaluated to implement appropriate safety measures.
Staff Training: The training of security personnel is essential for effective security management. Through Realview 4security, staff training and certifications are tracked, ensuring that guards are fully qualified and prepared to respond appropriately to any situation.
3.4 Field Security

iAlert Facility is an advanced personnel management solution in the security sector, designed for Android and Apple devices. Its primary goal is to enhance patrol planning management by providing real-time information on the location and status of the user/guard/employee.
What makes iAlert Facility stand out is its integration with Realview 4security, the central platform that enhances its capabilities.
Key Features:
- Real-Time Geolocation: iAlert Facility allows managers to track the exact location of the user—guard or employee—in real-time. This feature is crucial for effective patrol management and quick incident response.
- Panic Alerts and Emergency Calls: In case of threats or emergencies, guards can activate panic alerts or make direct calls to the Security Operations Center (SOC) with a single tap, ensuring immediate responses.
- Sensor Integration: Utilizing the smartphone’s sensors, iAlert Facility automatically detects incidents such as falls, collisions, or prolonged inactivity beyond the allowed time limit, sending instant notifications to the SOC.
- QR Code and NFC Technology: Guards can scan QR codes or NFC tags along their patrol routes, ensuring adherence to predefined schedules and patrol paths.
Special features:
- Infrastructure & Security: The application’s core infrastructure is built on a serverless environment with a “zero trust” security policy. Communication is always encrypted, making the app faster, resistant to central equipment sabotage, and highly efficient even during sudden spikes in demand.
- Shift Handover: Using either a personal code or their ERGANI QR badge, the guard can log their working hours at a post and record the exact location of their shift. The data is automatically transferred to the Realview 4security central management software and then to the ERGANI system.
- SOC Notifications: The supervisor/manager can receive updates on selected incidents via email or push notifications. The SOC can also send push notifications to the guard, informing them about an event and tracking whether the message has been read, ensuring that the necessary information has been received.
- End-Client Updates: The End Client can receive real-time updates on selected incidents via the iAlertPLUS app or the RealviewNOW web application. This ensures immediate and independent visibility of patrols, reducing the workload for the SOC.
3.5 Security Efficiency:
Operational Effectiveness for Security Personnel:
The iAlert Facility simplifies daily tasks for security personnel. Its user-friendly design ensures easy navigation, allowing guards to focus on their primary responsibilities without dealing with complex technology.
Customizable Solutions:
Recognizing that security technology needs vary by company, iAlert Facility offers adaptable solutions. Whether deployed in hotel management, service companies, or security firms, it adjusts to the unique requirements of each client.
Accurate Route Tracking:
Advanced iAlert Facility features enable precise tracking of routes, visit sequences, and time logs, offering a detailed account of patrol movements, deviations, and checkpoints. Through Realview 4security, this data is transformed into actionable insights, empowering supervisors and SOC operators in decision-making.
Incident Signals & Response Time:
Analyze incident signal metrics and response times. The iAlert Facility records critical data on emergency signals, providing a comprehensive overview of how quickly guards respond to critical situations. Realview 4security converts these metrics into a framework for improved response strategies.
Performance Metrics & AI Integration:
Evaluate employee performance through built-in analytics within iAlert Facility. From timely checkpoint scans to overall patrol scores and guard assessments based on client-specific requirements, this data, when integrated into Realview 4security, serves as the foundation for performance-driven security strategies. Monthly reports can also automatically update the HR department, ensuring accurate payroll processing. Additionally, these quantitative insights train the AI model, allowing security service providers to elevate their operational capabilities.
Optimized Resource Allocation:
By decoding patrol statistics and utilizing AI-driven models, security services gain insights into resource optimization. Identify patterns, assess high-risk zones, and strategically position personnel using real-time data.
Proactive Decision-Making:
The combination of iAlert Facility statistics and Realview 4security’s analytics enhances security management through proactive decision-making. Anticipate challenges, address vulnerabilities, and develop security strategies that are not just reactive but preventive.
Quality Control Measures:
Reveal quality control levels embedded in Realview 4security analytics. From unauthorized post bypasses to real-time security staff reassignment in case of an incident, the iAlert Facility app facilitates a meticulous quality control framework, ensuring security services are delivered to the highest standards.
4. IoT Module
 IoT device management is simplified with the right software and backend services that ensure data encryption, device status monitoring, and smooth application of updates. Realview 4security offers a complete set of tools that enhance your business capabilities.
IoT device management is simplified with the right software and backend services that ensure data encryption, device status monitoring, and smooth application of updates. Realview 4security offers a complete set of tools that enhance your business capabilities.
4.1 IoT Device Management
Registry Logging: Each device is integrated into the central system, along with its encrypted communication keys, operational rules, and designated control points. The system links IoT devices to specific projects and clients, ensuring that the infrastructure meets all necessary requirements and coverage areas.
Geolocation (GPS): Realview 4security utilizes GPS technology to track the real-time location of IoT devices. This enables immediate alerts in case of relocation, theft, or malfunction.
IoT Device Reports: The system generates detailed reports that include signaling data, executed or pending commands for each IoT device, and observations on any incidents or malfunctions. These reports are available for analysis by project or business administrators.
4.2 Benefits
Improved Management: Geolocation and detailed reports enhance the efficiency of IoT devices, optimize resource utilization, and enable performance monitoring.
Reduced Response Time: Real-time tracking of IoT devices minimizes response time in emergency situations, ensuring a swift reaction from the intervention team.
Enhanced Transparency: IoT device reports provide full transparency in task execution, facilitating service evaluation by clients.
4.3 Maintenance
Here, you can manage IoT device upgrade programs (patches), track their locations, and monitor the sequence and duration of each update. You can conduct historical audits and evaluate the results to ensure optimal performance and cybersecurity protection.
Maintenance is the core function of IoT devices in this section. The registration and monitoring of IoT device operations are conducted accurately and in real-time through Realview 4security.
4.4 Security Safeguarding
Security is the foundation of the Company's operations. Realview 4security and the IoT module work together to provide the most advanced tools for monitoring and managing the security of facilities, devices, and personnel.
4.5 Data Security
Data Protection: Both Realview 4security and the IoT module adhere to strict security protocols to safeguard customer and employee data. All information is stored in encrypted, secure databases with protection against external threats.
Facility Security: Continuous monitoring of facilities through IoT devices ensures a safe environment, promptly detecting and responding to threats such as intrusions or sudden anomalies in measurements.
5. Identity Verification Module
 Security service providers often handle user and system authentication. With Realview 4security and the Authentication module, this process becomes streamlined. The provided software and support services ensure real-time monitoring of user and device status, enforcing smooth access control and rights management. The goal is always to enable fast, hassle-free, and highly secure operations across the entire security infrastructure.
Security service providers often handle user and system authentication. With Realview 4security and the Authentication module, this process becomes streamlined. The provided software and support services ensure real-time monitoring of user and device status, enforcing smooth access control and rights management. The goal is always to enable fast, hassle-free, and highly secure operations across the entire security infrastructure.
The Zero Trust approach is a cybersecurity model based on the principle of "never trust, always verify." This means that no user or device, whether inside or outside the corporate network, is automatically considered trustworthy.
The core principles of Zero Trust are:
1. Least Privilege Access, users and devices receive only the minimum necessary access for their functions.
2. Continuous Verification, all users and devices must be continuously verified through multi-factor authentication (MFA)[8] and dynamic access policies.
3. Microsegmentation. The network is divided into smaller, secure segments to limit the spread of threats in case of a breach.
4. Monitoring & Threat Detection. Continuous analysis of user and device activity aims to detect suspicious behavior.
5. Assume Breach Model, security design operates under the assumption that a breach has already occurred, implementing measures to contain potential damage.
The Zero Trust approach helps organizations protect against cyberattacks, insider threats, and data breaches by enforcing strict access control and continuous monitoring. Realview 4security provides a comprehensive set of tools that enhance these capabilities.
[8] (MFA-Multi Factor Authentication)
5.1 Management of Identities & Access Roles
Users and devices receive only the strictly necessary access for their operations. Each user or device is integrated into the general access control system, which includes encryption keys for communication, operational roles governing them, and control points serving each use case.
At the same time, their behavior is thoroughly monitored, not only in terms of the resources they utilize and their associated costs but also for any potential violations. For example, if a user attempts to delete a file, the system will prevent the action while logging it as an event and notifying the appropriate authority.
5.2 Identity Verification
Every access attempt must be continuously verified, even for users who are already logged in. Multi-factor authentication (MFA, OTP[9], etc.) is used to ensure that the user is who they claim to be. The system responds dynamically to user or device behavior. For example, if a user suddenly downloads a large volume of data, the system may either block them or require re-authentication.
[9] OTP-One Time Password
5.3 Microsegmentation
Realview 4security consists of completely separate system entities within a multi-tier network and infrastructure setup (VPCs, subnets, security groups). The network is divided into smaller segments, ensuring that a breach in one section does not grant access to the entire network. This prevents attackers from freely moving within the system. The same approach applies whether it’s a client system that needs permissions to access resources, individuals working with specific software or files, or a combination of both.
Following AWS architectural protocols, Realview 4security operates within closed communication networks, without internet access and with encrypted network configurations at every system level. Each level ensures its own protection with a dedicated firewall and grants maintenance teams access only to the central machine’s software, not the Realview 4security source code or database. If internet access is required, special encryption measures are implemented, and communications are closely monitored for anomalies, especially those involving critical data or unusual activity.
5.4 Anomaly Detection
If an employee or device that typically accesses specific files suddenly attempts to download entire databases, the system will detect and block the activity. All user and device activities are monitored in real time to identify suspicious actions. Artificial intelligence is used to recognize anomalies. The data is processed through security data collection and analysis from various network points. Additionally, user behavior analysis is conducted to detect suspicious actions, and if the system identifies unusual activity, it can automatically block the user or device and notify the appropriate authority.
5.5 Assume Breach Model
Realview 4security is designed with the assumption that an attack has already occurred or will happen in the future. This enables rapid response preparation and damage containment. It maintains backup copies of data, employs advanced isolation mechanisms (sandboxing), and conducts regular security testing to identify vulnerabilities. Similar cybersecurity response plans are shared with all Realview 4security clients and extended to end-users to ensure adoption and implementation.
6. Decision Maker Module

This module is designed to assess client directives and provide personalized responses effectively. It works in collaboration with artificial intelligence models and serves as the leading component of Realview 4security.
The development of action plans based on client instructions, their adjustment according to the expertise of the security company, and the final structuring of actions at each operational phase in the field environment are all integrated with artificial intelligence to deliver security solutions. The steps defined and processed within Realview 4security are as follows.
6.1 Risk Analysis
• Identification of potential threats (physical, technological, human).
• Assessment of the likelihood and impact of each threat.
• Determination of critical points that require protection.
We identify potential threats (natural disasters, cyberattacks, human errors) and evaluate their probability and impact. These are recorded in Realview 4security with weighted factors for each point, and response teams are assigned accordingly.
6.2 Risk Mitigation Strategies
• Recommendations for technical or organizational security measures.
• Enhancement of physical or cybersecurity based on specific needs.
• Development of incident response procedures.
At this stage, we precisely define prevention and response measures, such as physical security (cameras, guards), cybersecurity (firewalls, encryption), and staff training. We evaluate the effectiveness of each measure and how well our response can perform based on incident history and similar past events. Realview 4security assigns a score to the framework, and we structure actions into steps. Finally, standardized action scenarios are prepared to train the operations center and field teams.
6.3 Cost & Benefits
• Analysis of the implementation cost of security measures in relation to their benefits.
• Optimization of resources for more efficient security.
At this stage, we calculate the cost of each security measure and compare it with its benefits to determine the optimal balance between investment and protection. Depending on the scenario, cost tables and corresponding measures are proposed.
6.4 Regulatory Compliance
• Verification that decisions align with legal and regulatory requirements.
We ensure that security measures comply with legal and regulatory requirements (GDPR, ISO 27001, local laws). Any deviations are noted, and reminders are set for the operations center and company management to achieve compliance.
6.5 Decision-Making Support
• Development of scenarios for different security strategies.
• Presentation of the advantages and disadvantages of each option.
• Assistance in the final selection based on objective criteria.
In Realview 4security, we present different scenarios and the consequences of each choice to support informed decision-making based on objective data. This is done both in a simulation environment for training the operations center and in real-time to respond to emergency situations.
Conclusions
The use of Realview 4security software and AWS infrastructure enables the company to provide high-quality services while continuously improving operational efficiency and security. Through comprehensive data management, increased transparency, enhanced security, and real-time access to information, the company ensures that its services meet the highest standards and customer requirements.
Key Features of Realview 4security:
Technological Superiority: Utilizes ORACLE, AWS Cloud, IoT[10], and Artificial Intelligence (AI) for advanced security management.
System Modules:
1. Monitoring: Real-time surveillance of security systems.
2. Human Resource Management: Personnel monitoring, shift management, and certifications.
3. Patrolling: Security management and tracking, GPS tracking.
4. IoT: Integration and management of smart devices.
5. Authentication: Implementation of Zero Trust policies for data security and controlled user access.
6. Decision-Making: Analysis and security action recommendations using empirical models or AI.
Compatibility & Flexibility: No special equipment required; operates on AWS Cloud with hybrid options for clients.
Regulatory Compliance: Integrated with the ERGANI information system and NIS2 directive.
Realview 4security is a modern SOAR (Security Orchestration, Automation & Response) solution that integrates PSIM, SIEM, and AI technologies, offering comprehensive security management for businesses. Reform's investments in technology and ongoing innovation make the company one of the most reliable and effective in the field of asset and facility security, providing solutions that meet the modern market's demands.
[10] ΙοΤ (Internet of Things)
Proposals
For the optimal implementation of Realview 4security in a security and cyberattack protection company, emphasis should be placed on the system’s unique advantages and its application should be tailored to the specific needs of the business.
Together with the SOC team and the end client, the following four key points of the solution’s strategy will be analyzed:
A. Focus on the Needs of the End Client
✔ Physical Security → Patrol monitoring, incident management, live camera feed.
✔ Cybersecurity → Risk management, threat detection and response, integration of a Zero Trust policy.
✔ Automated Personnel Management → Shift control, compliance with legislation (PS ERGANI).
B. Solution Customization
o Personalized Presentation → Focus on patrols, risk management, and facility monitoring.
o Cost and Performance Calculation → Demonstrating savings through automation and error minimization.
o On-Site Testing (Proof of Concept) → Deployment of a pilot project in selected facilities.
C. Implementation Methods in the Security Company
C.1 Integration into Daily Operations
✅ Process Digitization → Replacing outdated Excel files with automated patrol and security management.
✅Integration with Existing Systems → Unification with ERP, payroll software, cameras, alarm systems, and IoT equipment.
✅ Staff Training → Conducting workshops for management, security guards, and security administrators.
C.2 Adaptation to Cybersecurity Requirements
🛡 Zero Trust Access Control → Restricting access for personnel and suppliers.
🔐 Data Protection → Implementing encryption and SIEM for early attack detection.
📊 Compliance Reports → Automated reports for NIS2, GDPR, and PS ERGANI.
D. Promotional Actions for the End Client
📢 Marketing & Case Studies → Showcasing successful implementations in other businesses.
💬 Negotiation Focused on Cost Savings → Demonstrating reduced management costs and improved efficiency.
🔄Flexible Payment Model Offering (SaaS[11] Subscription or Hybrid Solution) → Subscription-based sales or on-premise customization.
[11] SaaS=Software as a Service